Using BURP to Brute Force Damn Vulnerable Web Applications
To a knowledgeable information security professional, Damn Vulnerable Web Applications is just as it sounds. It is a set of purposefully flawed web applications that allows a pen testers to practice his or her craft. In this demonstration, I am going to be using Burp Suite to brute force the username and password on a DVWA authentication form field.
As a disclaimer, this demonstration is solely proof of concept. This blog does not condone or encourage any type of malicious behavior. Also, this article is just a demonstration on how to use a part of Burp Suite. Honestly, I am mainly writing this article for the purpose of educating myself. Now that that’s out of the way, let’s get started.
First, make sure you have DVWA up and running. Initially you will have to log in using the username and password of admin:password. On the left, in DVWA Security section, set the security level to low. After the security has been lowered, select the “Brute Force” challenge on the left side column as shown in the picture below.
Before starting Burp Suite, we need to make sure that the a local proxy server is up and running on your local web browser. Below is a screen shot of how a local proxy server should be configured on Firefox.
For this demonstration Burp Suite is running on the on Windows 7 environment. As long as the latest version of Java is installed on your local computer, launching Burp Suite is as simple as double clicking the “burpsuit_free_v1.5.jar” file. Once you double click this file, it will open a window that looks like the one below.
Now that Burp Suite is running, we can start doing some of the fun stuff. If setup correctly, BURP should already be intercepting traffic (which has the ability to halt your local internet traffic). We now need to revisit our DVWA Brute Force page. While in the Brute Force page, enter a bogus username / password combination and click ‘Login’. This will allow us to capture an authentication request being sent through the wire.
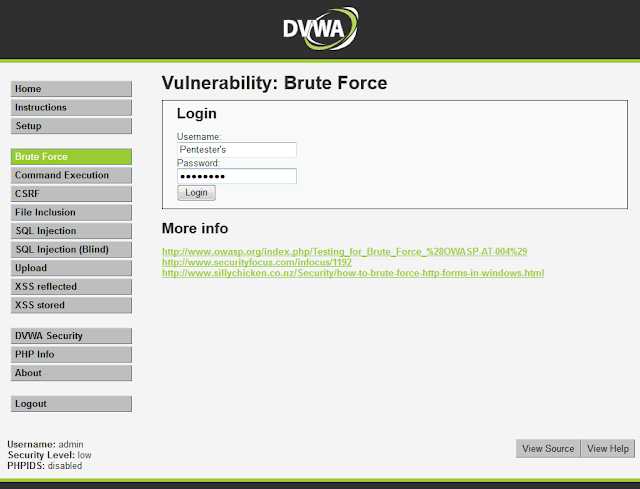
A successfully captured authentication request will look like the screenshot below. In this example the username is Pentester’s and the password is Paradise. Right click anywhere within this white window and select Send to Intruder.
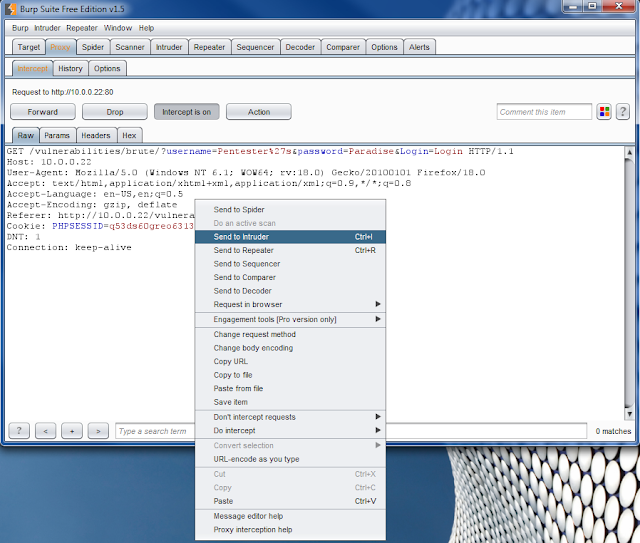
Below shows the captured authentication request that we the user forwarded to the Intruder section of Burp Suite. Burp Suite is very intelligent tool and automatically attempts to highlight any fields it may find relevant. In this scenario, we will be only concentrating on username and password. All other fields need to be cleared. First, click the clear button on the left side of the window. This will remove all the pre-selected orange highlights. Highlight the fields after “username=” and “password=” and click add (In this case it was “Pentester’s” and “Paradise”).
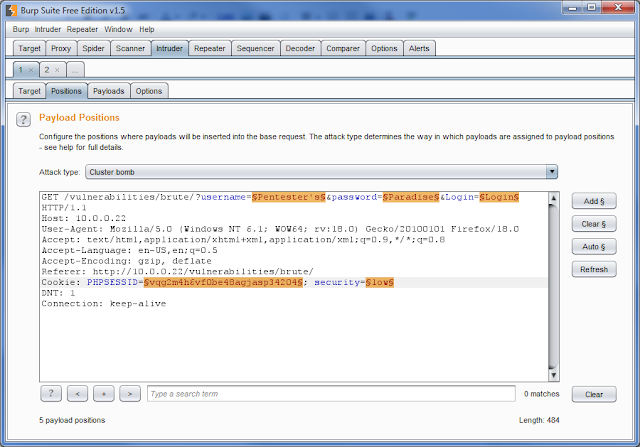
If done correctly, the positions should be highlighted like the picture below. Make sure that the Attack type is set to Cluster Bomb. For more information on attack types, visit here.
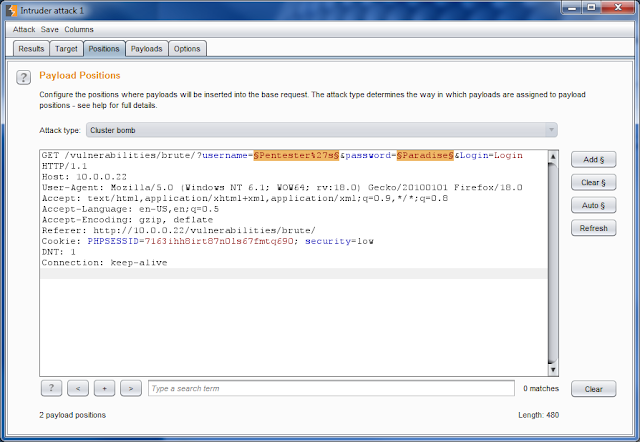
Now that we have the correct fields specified. We will begin by setting up the payloads by clicking thePayload tab. Make sure Payload Set is set to 1 and the Payload type is set to Simple List. Below begin to manually entering possible usernames in Enter New Item field and click add for each one. Unfortunately, if you are using the free version of Burp Suite, you are unable to load any per-defined dictionary lists.
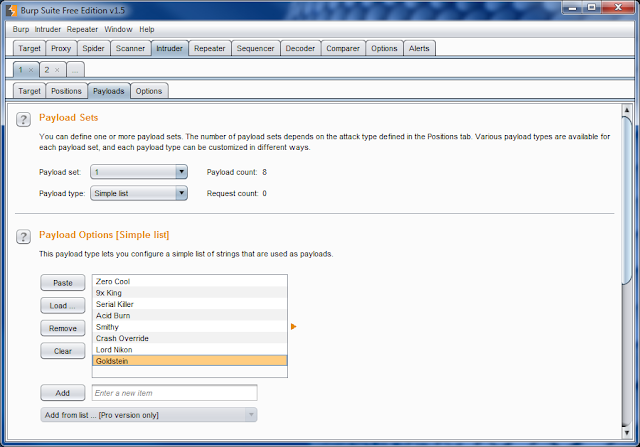
Now that we have the multiple usernames established, we need to setup the multiple passwords we want to try. In the Payload Set drop down, select number 2. Keep the Payload Type as Simple List. Now add some probable passwords.
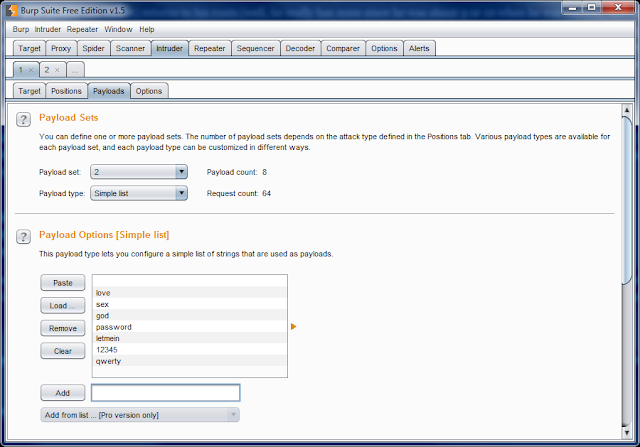
Now it’s time to try out our newly configured attack. Simply start the attack by going to Intruder and clicking Start attack.
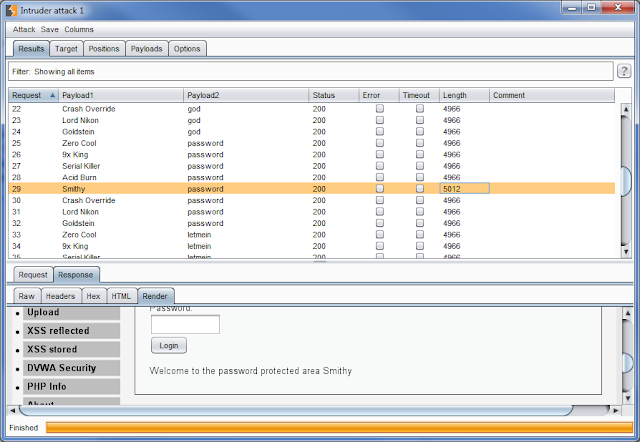
*Spoiler* – After the attack has been started, you will see Burp trying to use every possible username and password. In this scenario, we are able to see that the username Smithy and the password ofpasswordgenerate a response length that is different from all other attempts. In this scenario it is an indicator that the username and password are correct. Click the Response tab then click the render tab to see that our dictionary attack has proven successful.
Final Thoughts:
I found this exercise to be a interesting proof of concept and a valuable learning experience. If an attacker has a large dictionary file and ample time, this is almost a fool proof method of thwarting basic authentication on misconfigured web applications.
But how do we fix it?
The best way of defeating a brute force attack like the one would be implementing account lockout/cool down capabilities within the web application. Another great way to defeat this brute force process is by implementing a 3rd authentication method such as CAPTCHA.
References
I didn’t think of this exercise all on my own. I must give credit to the following blog for the idea:
http://pentestlab.wordpress.com/2012/12/21/brute-force-attack-with-burp/
Thành Long
Nguồn: anninhmang.net













0 nhận xét:
Đăng nhận xét